A SOC Odyssey - Windows Event IDs Writeup
Question 1: Your Support Team has been hacked and the workstations remotely accessed. The attacker used a well-known windows protocol to gain access. Your mission, should you choose to accept it is as follows: As the SOC analyst on duty, which Event ID will help you identify the attackers’ remote access event assuming the attacker was able to successfully login? Enter the Event ID only
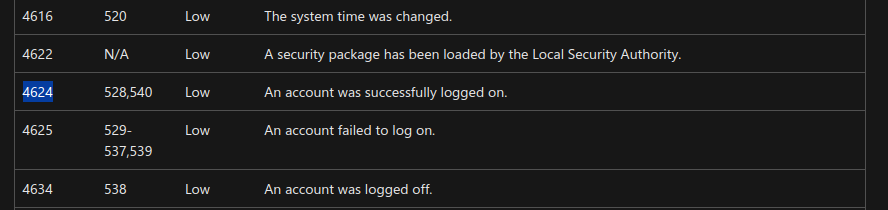
From our knowledge, we know that definitely the well-known protocol being refereed to is Remote Desktop Protocol. Digging a little on the internet, we find an event id 4624 that indicates successful logon
Question 2: Enter the port number of the protocol abused by the attacker
RDP uses port 3389
Question 3: After installation, the attacker seems to have downloaded an .exe file and installed it on the infected workstation. Your mission, should you choose to accept it is as follows: As the SOC analyst on duty, which Event ID will help you identify the file name and location the attacker downloaded?
With research, we find that when a file is created or downloaded, a sysmon event FileCreate is called and its ID is 11
Question4: Based on the previous question, your mission, should you choose to accept it is as follows: As the SOC analyst on duty, which Event ID will help you identify the URL from which the attacker downloaded the file
There is an event by sysmon that indicates network connections, including the destination addresses and ports, which can help you identify URLs involved in the download. It is event ID 3
Question 5: After the download of the file, the attacker proceeded to install the executable. Your mission, should you choose to accept it is as follows: As the SOC analyst on duty, out of the box, will we have an Event ID generated for this ? (YES or NO))
No. Because, out of the box, Windows does not generate an Event ID specifically for the installation of an executable file
Question 6: After the executable file was downloaded. It was executed and new processes created. Which Event ID can help us identify these events?
There would be a newly generated process, hence an event ID 1
Question 7: Most malware will try to connect to a C2 server. At times, this C2 servers use domains generated by DGA. You need to find the domains the malware might tried to reach. Which Event ID will help you with this
Malware uses DNS in the traditional way to locate components of the attacker infrastructure such as command and control servers. Hence, a DNSEvent would be generated that has id 22
Question 8: The Windows Defender malware protection scan service was canceled when it tried to scan the malware. You need to find out the time the scan was canceled. Which Event ID will help you pick this event
I definitely thought this was 1116 because it deals with Windows Defender, but it isn’t. Doing more research, I find a port 1002 that is generated when an application hangs or becomes non-responsive
Question 9: Had the above scan detected the malware. What Event ID would you be looking for?
This would be event ID 1006, that indicates a Group Policy update has failed
Question 10: The attacker shutdown the workstation when they completed the attack. Which Event ID will help us pick the shutdown event?
This is event ID 1074, System has been shutdown by a process/user
So much to brush on Windows Event IDs and much more to learn from the module!!